- Nosql Injection Cheat Sheet
- Nosql Injection Cheat Sheet Printable
- Pentestmonkey Sql Injection Cheat Sheet
NoSQL injection refers to an injection attack through the placement of malicious code (like other web attack ways) in NoSQL statements through web page input controls. Considering that the structure (or actually the non-structure) of NoSQL databases is very different from structured databases like MySQL, MSSQL or PostgreSQL. Are their known tools, payload lists, tricks or other common practices (other then using a creative hackers-mindset), in order to test if a application is vulnerable to NoSQL injections?
Serialization is the process of turning some object into a data formatthat can be restored later. People often serialize objects in order tosave them to storage, or to send as part of communications.Deserialization is the reverse of that process -- taking datastructured from some format, and rebuilding it into an object. Today,the most popular data format for serializing data is JSON. Beforethat, it was XML.

However, many programming languages offer a native capability forserializing objects. These native formats usually offer more featuresthan JSON or XML, including customizability of the serializationprocess. Unfortunately, the features of these native deserializationmechanisms can be repurposed for malicious effect when operating onuntrusted data. Attacks against deserializers have been found to allowdenial-of-service, access control, and remote code executionattacks.1
Nosql Injection Cheat Sheet
Challenges covered in this chapter
| Name | Description | Difficulty |
|---|---|---|
| Blocked RCE DoS | Perform a Remote Code Execution that would keep a less hardened application busy forever. | ⭐⭐⭐⭐⭐ |
| Successful RCE DoS | Perform a Remote Code Execution that occupies the server for a while without using infinite loops. | ⭐⭐⭐⭐⭐⭐ |
ℹ️ Please note that both RCE challenges described below are notavailable when running the Juice Shop in either a Docker container oron a Heroku dyno! The deserialization actually happens in a sandbox witha timeout, but with sufficient skills an attacker could break out of thesandbox and actually harm the underlying system. While it is unfortunateto not have RCE challenges on containerized environments, thisillustrates how hard it is to protect against deserialization attacksexcept for not using it at all.
Perform a Remote Code Execution that would keep a less hardened application busy forever
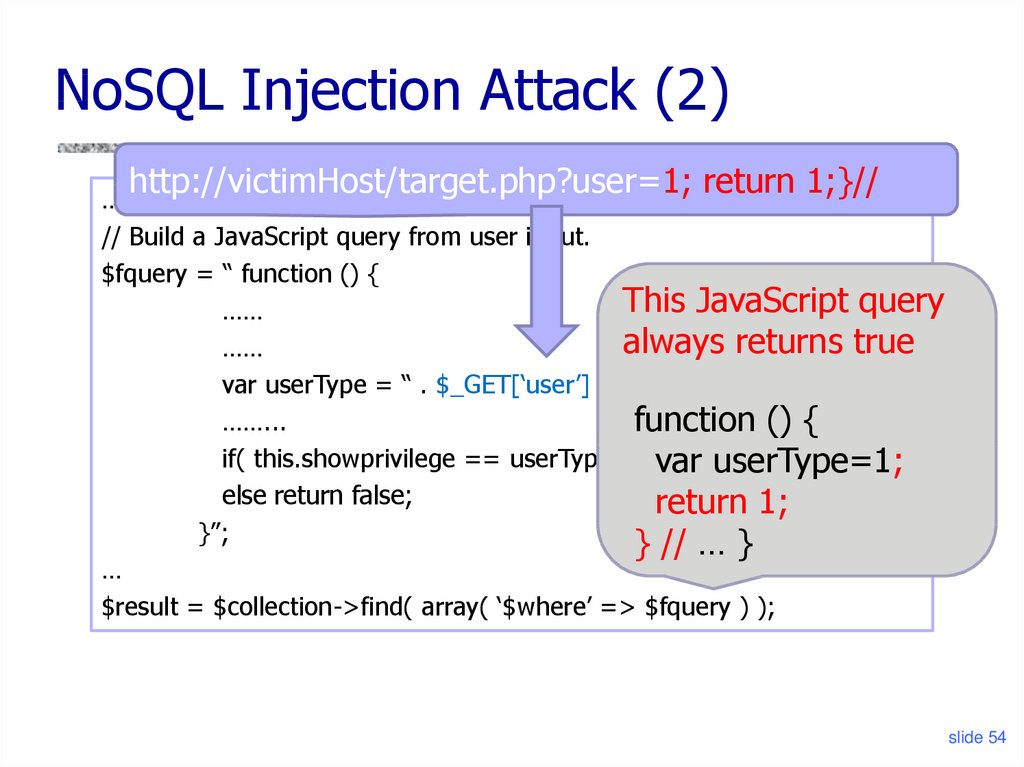
Code Injection is the general term for attack types which consist ofinjecting code that is then interpreted/executed by the application.This type of attack exploits poor handling of untrusted data. Thesetypes of attacks are usually made possible due to a lack of properinput/output data validation, for example:
- allowed characters (standard regular expressions classes or custom)
- data format
- amount of expected data
Code Injection differs from Command Injection in that an attacker isonly limited by the functionality of the injected language itself. Ifan attacker is able to inject PHP code into an application and have itexecuted, he is only limited by what PHP is capable of. Commandinjection consists of leveraging existing code to execute commands,usually within the context of a shell.2
The ability to trigger arbitrary code execution from one machine onanother (especially via a wide-area network such as the Internet) isoften referred to as remote code execution.3
- The feature you need to exploit for this challenge is not directlyadvertised anywhere.
- As the Juice Shop is written in pure Javascript, there is one dataformat that is most probably used for serialization.
- You should try to make the server busy for all eternity.
- The challenge will be solved if you manage to trigger the protectionof the application against a very specific DoS attack vector.
- Similar to theLet the server sleep for some timechallenge (which accepted nothing but NoSQL Injection as a solution)this challenge will only accept proper RCE as a solution. It cannot besolved by simply hammering the server with requests. That wouldprobably just kill your server instance.
Perform a Remote Code Execution that occupies the server for a while without using infinite loops
An infinite loop (or endless loop) is a sequence of instructions in acomputer program which loops endlessly, either due to the loop havingno terminating condition, having one that can never be met, or onethat causes the loop to start over.4
- This challenge uses the same leverage point asPerform a Remote Code Execution that would keep a less hardened application busy forever.
- The application has a protection against too many iterations (i.e.infinite loops) which your attack must not trigger in order to solvethis challenge.
1. https://owasp.org/www-project-cheat-sheets/cheatsheets/Deserialization_Cheat_Sheet.html ↩
2. https://owasp.org/www-community/attacks/Code_Injection ↩
3. https://en.wikipedia.org/wiki/Arbitrary_code_execution ↩
Nosql Injection Cheat Sheet Printable
Pentestmonkey Sql Injection Cheat Sheet
4. https://en.wikipedia.org/wiki/Infinite_loop ↩
